-
Notifications
You must be signed in to change notification settings - Fork 143
Home
Welcome to the WMImplant wiki!
The first thing you will need to do is import the WMImpant.ps1 on the console that you are using (PowerShell, Beacon, Empire, Meterpreter, etc.). Importing the script is an exercise I feel comfortable leaving to the user.
After having imported WMImplant, you have two ways that you can use the tool, interactively or non-interactively. Using WMImplant in a non-interactive manner will allow you to script actions with WMImplant, and/or use it in a RAT of your choice.
Looking for the easiest way to get running fast? Just import and run "Invoke-WMImplant"
WMImplant is a tool that's designed to completely use WMI. WMI is not only the mechanism for triggering actions on the targeted machine, but it is also the C2 channel itself. Where required, WMImplant stores data in WMI properties, but in one situation it stores data in the system registry. When interacting with WMI properties, WMImplant captures the original property value, modifies the value, and then restores the original value once it is complete. When interacting with the registry, WMImplant creates a new registry key, stores the data in the registry value, retrieves the data, and then removes the key. For specifics on where data storage is required, and how data is stored for each command, please review the respective commands in the Commands section.
This section will go over the different commands that WMImplant supports and how WMImplant performs each command.
The change_user command enables you to change the user context that you are currently running as. By default, WMImplant will run in the context of the user account that starts the tool. However, if you need to change the user account context you are running as, you can easily do it with the change_user command. WMImplant will prompt you to provide the new user account (DOMAIN\account) and password that you wish to authenticate with. From that point on, WMImplant will use the new account credentials (unless you use the change_user command again, or exit WMImplant).

This command exits WMImplant.
This is an incredibly useful command for when you want to use WMImplant in a non-interactive manner, but don't know the command line flags to use. If that is the case, use the gen_cli command. Once you run this command, the normal help menu will pop up. Select the command you want to use in a non-interactive manner. WMImplant will then prompt you to answer questions that it will require when running this command from the command line. After you've answered every question, WMImplant will produce the command line command you should run. At this point, just copy and paste the command, and run it!
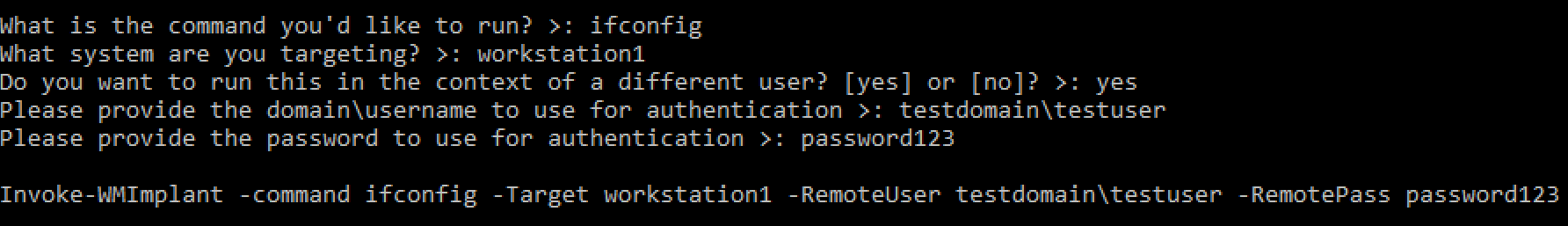

This command shows the WMImplant menu.
This command reads the contents of a user-specified file on the targeted machine. This works by invoking PowerShell on the remote machine, reading in the specified file, encoding the file contents, storing the encoded contents in a WMI property, reading the WMI property from the attacking machine, decoding and writing the contents to disk, and replacing the WMI property with its original value. The WMI property being used has stored more than 200 megabytes of data previously, however I wouldn't recommend it. For large files, it is likely better to completely download the file than trying to read the contents with the cat command.

This command allows you to download a file from the targeted system onto your attacking machine. This works by starting PowerShell on the targeted system, reading the specified file, encoding its contents and storing them in the targeted system's registry. The attacker's system then makes a second WMI query to retrieve the contents of the registry value storing the file. The attacker's system then decodes the contents, writes it to disk on the attacking machine, and issues a final WMI command deleting the registry value that was holding the file.

This command lets you get a directory and file listing of any directory that you specify on the targeted machine.

This command spawns PowerShell on the targeted machine, uses the IEX command to download the Invoke-Ninjacopy script in memory, and then copies the user specified file to the user specified location.

The search command enables the user to search for a specific file, or multiple files, on the targeted machine. It also allows you to search by file extension if that is the preferred method. If the file is found, or any file with the extension that the user is searching for, it's location will be returned to the console.

This command allows the user to upload a file from their machine to the targeted machine. The attacker's machine spawns PowerShell which reads the contents of the file the attacker would like to upload, encodes the contents, and stores the encoded contents in the attacker's system's registry. Then, WMImplant spawns PowerShell on the targeted machine, which makes a WMI query against the attacker's system to obtain the registry key's value containing the encoded file. The targeted machine then decodes the contents and writes the file to disk.
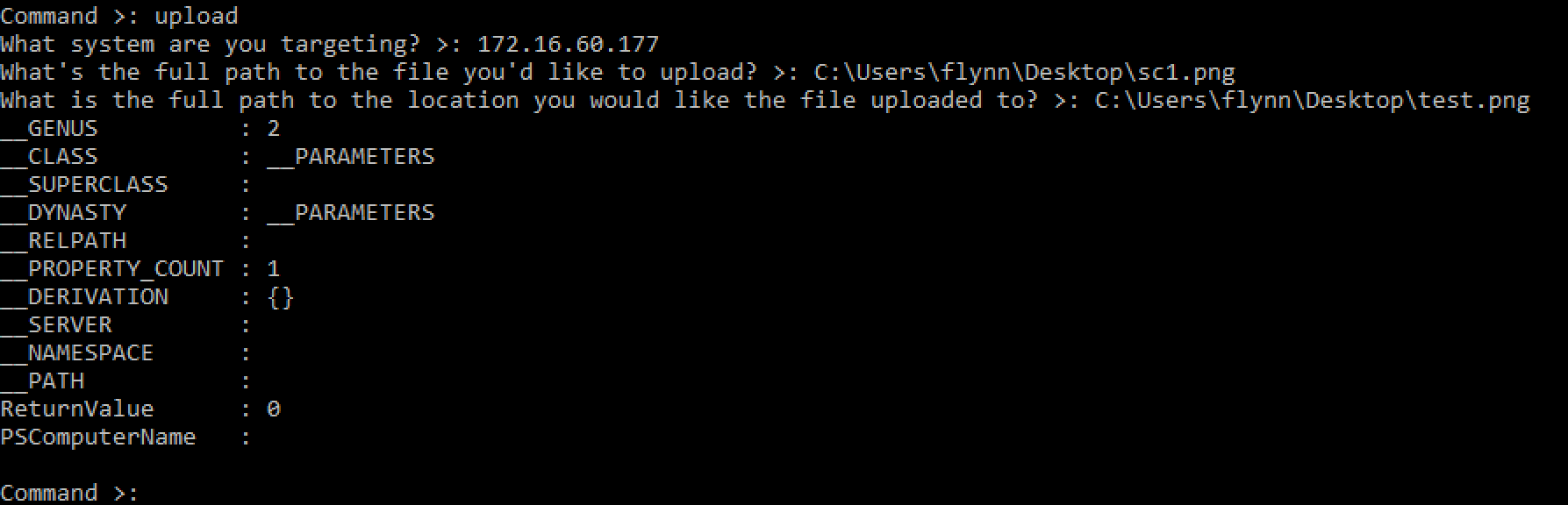
This command allows the user to run a command on the targeted machine and receive its output. The command is any command-line command, such as ping, nslookup, nltest, etc. The attacking machine spawns PowerShell on the targeted system which runs the user-specified command. The command's output is encoded and stored in a WMI property. The attacking machine queries WMI for the property storing the output, decodes the output, displays the output to the console, and replaces the WMI property with the original value.

This command modifies the targeted system's registry and sets the UseLogonCredential key to have a value of 0 via WMI.
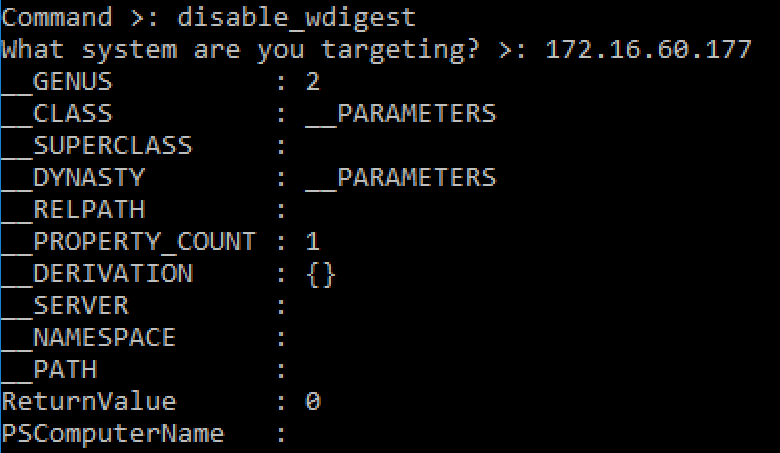
This command starts PowerShell on the targeted system and attempts to force disable WinRM.
This command modified the targeted system's registry and sets the UseLogonCredential key to have a value of 1 via WMI.

This commands starts PowerShell on the targeted system and attempts to force enable WinRM.
This command enables the user to modify the registry on the targeted system over WMI. You can create or delete registry keys, however if creating a key it can only be of type STRING currently. If there is a good use-case for updating this, I will be happy to modify the code (or accept a pull request :)).
This command enables the user to run any PowerShell script on the targeted host and receive its output. The attacking machine starts PowerShell on the targeted system which IEX downloads a user specified PowerShell Script, a user-specified function is ran and its results are encoded and stored in a WMI property. The attacking machine then queries the specific WMI property to retrieve the encoded results, decodes the results, displays the results to the console, and replaces the WMI property with the original value.

This command enables the user to create, list, or delete scheduled tasks on the targeted system over WMI.
This command enables the user to start, stop, create, and delete services on the targeted system over WMI.
This command is an alias for "Invoke-Mimikatz". The attacking machine will spawn PowerShell on the targeted system, IEX download Invoke-Mimikatz, run "Invoke-Mimikatz", encode the results and store them in a WMI property. The attacking system then makes a second query retrieving the encoded results, decoding them, displaying the results to the console, and replaces the WMI property with the original value.
This command allows the user to kill a process on the remote system by name or process ID over WMI.

This command allows the user to start a process on the remote system over WMI.

This command displays all running processes from the targeted machine on the attacking computer over WMI.
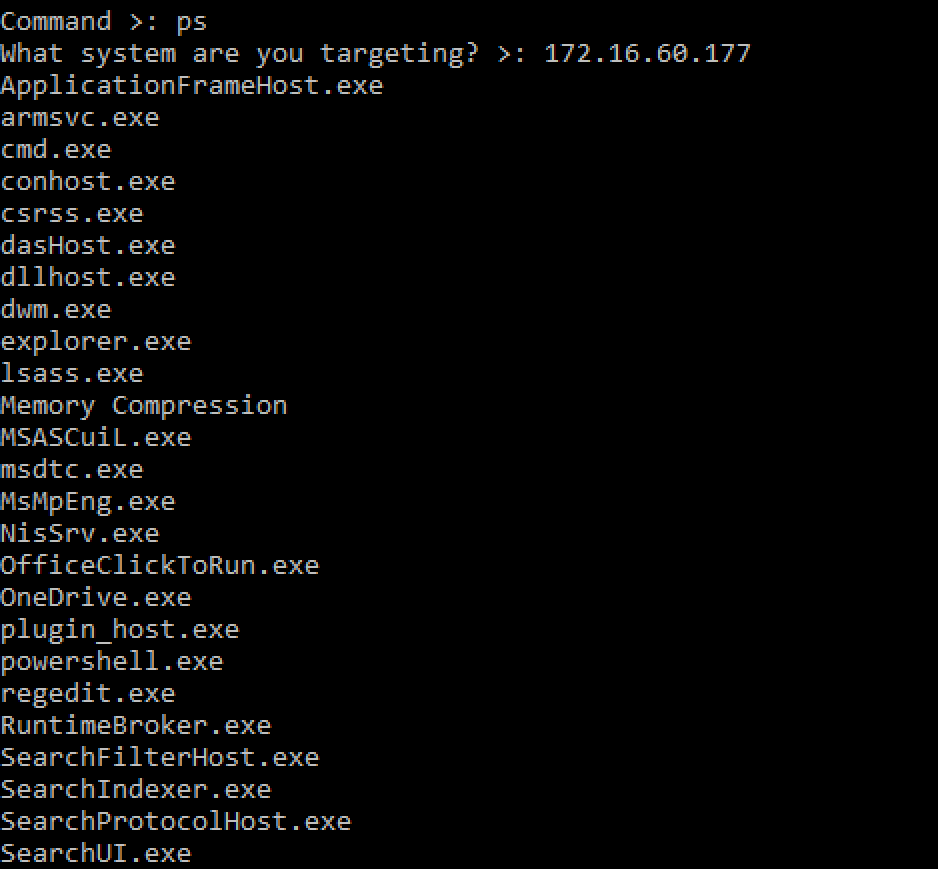
This command gathers all the running processes on the targeted systems and lists the accounts that own the running processes over WMI.
This command gathers very basic information about the targeted system over WMI.

This command attempts to list all physical and network drives attached to the targeted system over WMI.

This command enumerated all NICs on the targeted system that have an active IP address. Each NIC with an active IP address is displayed to the console.

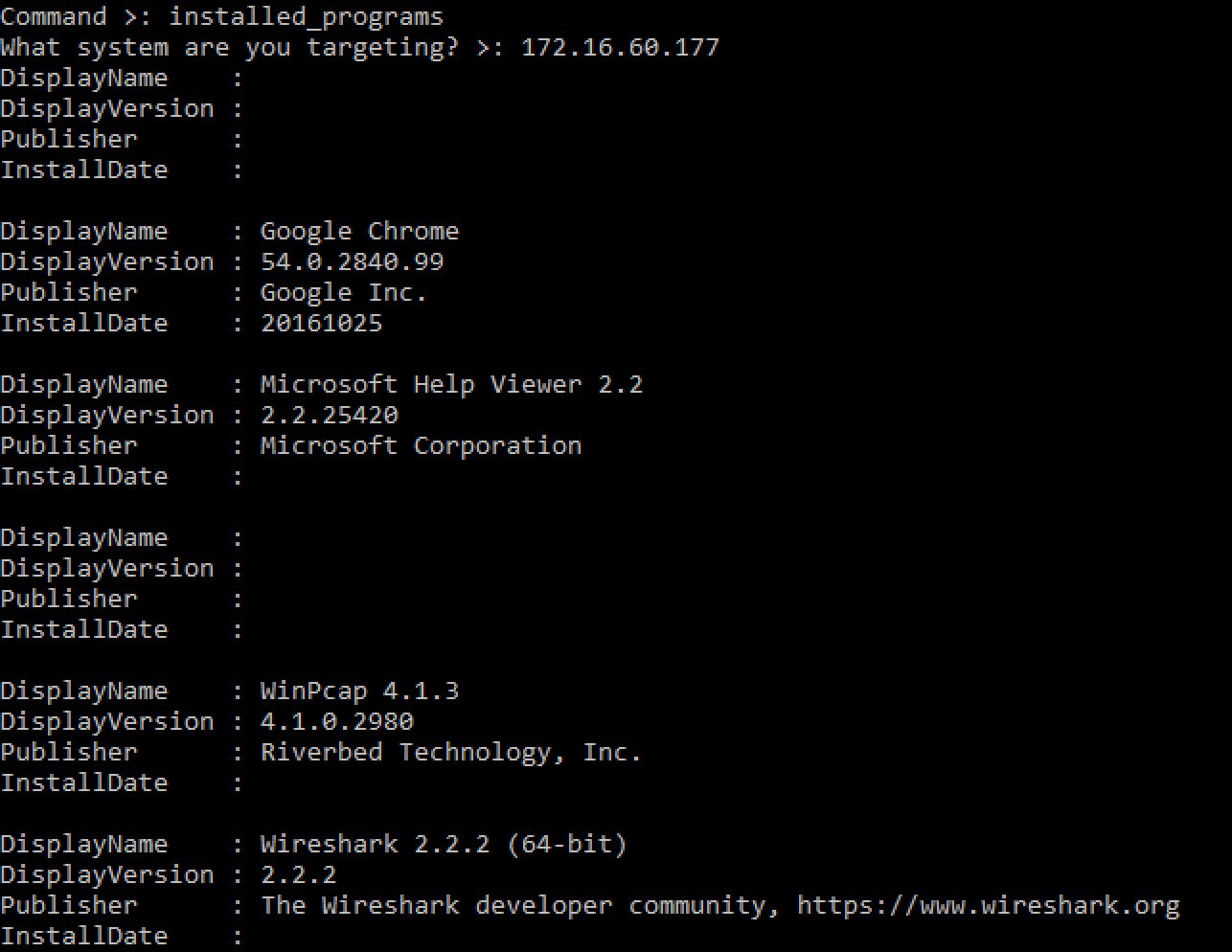
This command enumerates the applications which have been installed on the targeted system. The results are encoded and stored in a WMI property. The attacking system makes a WMI query to receive the encoded results, decodes the results, displays the contents to the console, and sets the WMI property back to it's original value.
Uses a WMI command to log users off the targeted system
Uses a WMI command to reboot the targeted system
Uses a WMI command to power off the targeted system
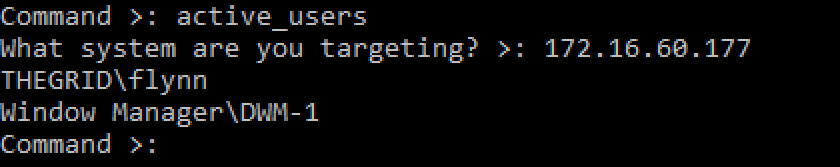
This command attempts to determine if a user is actively using the targeted system. First, it tries to determine if a screensaver is active on the system, and displays the results. It then tries to pull user information from the system with a second WMI query and displays any potential active user information.

This command parses the event log on the targeted system to find user accounts that have logged onto the targeted system.